To collect logs from the Okta platform, if you are not using the Sumo Logic FedRamp deployment, use the new Cloud to Cloud Integration for Okta to create the source and use the same source category while installing the app.
The sections below are deprecated for non-FedRamp Sumo Logic deployments. If you are using the Sumo Logic FedRamp deployment, use the sections below to configure collection for this app.This page provides instructions for setting up alog collection from Okta. Click a link to jump to a topic:
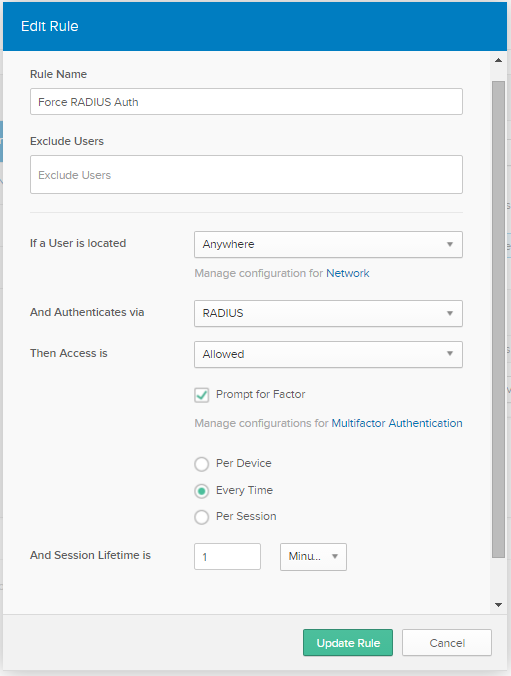
Hi, We have OKTA i have setup a radius server I configured Meraki to authenicate VPN with radius. When i test it out, it fails Okta wont prompt for MFA and wont login into VPN. When i disable MFA in OKTA i can login in VPN with Radius no MFA though. I have a requirement for MFA is this possible? Thanks for the great client! The AnyConnect server I'm using requires 2FA with Okta. When I'm specifying the TOTP secret key, openconnect doesn't use it in the 2FA form (private data is redacted): $ pass vpn head -n1 openconnect -v -u u -authenticate -passwd-on-stdin -token-mode=totp -token-secret='base32:$( pass totp )' -dump-http-traffic vpn.example.com 2&1 tee log POST https. Below is an example of how Okta interacts with a Cisco ASA VPN for Anyconnect RADIUS authentication protocol. The configuration for Okta is broken into sections: Group Setup and User Setup. Sign into Okta as an Admin; Click Admin button in upper right Click Security - Multi-factor from the top menu. Select the Juniper SSL VPN option. Support Announcement: Apple no longer supports Juniper VPN options on macOS Sierra.This is an Apple limitation. Okta will maintain this option, but will not support it with bug fixes. This includes the Learning Portal, Help Center, okta.com and other Okta web properties.
Requirements and process overview (DEPRECATED)
Before you begin setting up log collection, review the required prerequisites and process overview described in the following sections.
Prerequisites
- The integration between Sumo and Okta relies upon SumoJanus, a proprietary library used for script-based collection from applications such as Okta, Box, and Salesforce.
- The system where you deploy SumoJanus and configure your installed collector and script source must have Java.
JAVA_HOME environment or absolute PATH variable.Process Overview (DEPRECATED)
Setting up log collection from Okta for analysis in Sumo Logic includes the following tasks, which must be performed in the order in which they are presented.
- Generate an Authentication Token in Okta.
- Download the SumoJanus package necessary for authentication.
- Deploy the SumoJanus package on a local server running the Sumo Logic Collector.
- Edit the local properties file with the Okta token created in step 1. The Properties file will be generated in step 2 when you download and deploy the SumoJanus package.
- Configure an Installed Collector and
- Configure a Script Source in Sumo Logic to send the data from Okta to Sumo Logic.

Configuring Okta log collection (DEPRECATED)
This section walks you through the process of setting up log collection from Okta for analysis in Sumo Logic. Click a link to jump to a topic.
Step 1: Generate the Okta API token (DEPRECATED)
Create an Okta API token, following instructions in Okta help. You will add the token to the SumoJanus properties file, later in this procedure.
Step 2: Download the SumoJanus package (DEPRECATED)
The following SumoJanus file is required to collect logs from Okta. Download the appropriate file for your system.
| Linux | Windows | |
|---|---|---|
| SumoJanus v3.0.1 package file | sumojanus-okta-dist.1.0.2.tar.gz | sumojanus-okta-dist.1.0.2.zip |
Step 3: Deploy the SumoJanus package (DEPRECATED)
If you have not previously set up SumoJanus, follow the steps in New SumoJanus installation. If you have previously set up SumoJanus, follow the instructions in SumoJanus installation update.
New SumoJanus installation
Copy the package file you downloaded in Step 2 to the appropriate sumojanus folder, then unzip them there.
Okta Anyconnect Download
- On Linux, run the following command:
- On Windows, you can use Windows Explorer to open the zip package and copy it to the appropriate target folder.
Update your SumoJanus installation
- Backup conf/sumologic.properties and the data folder.
- Setup a New SumoJanus installation
- Migrate the backed up conf/sumologic.properties and data folder to the new Janus folder
- Modify the paths in Step 6 below to point to the new folder.
Step 4: Edit the Properties file (DEPRECATED)
- Open the file
<sumojanus_foldername>/conf/sumologic.propertiesin a text editor and add the following lines to the end of the file. You will replace the <variables> with information (including the brackets) you enter in the following steps.
- api_token. Enter the Okta API token that you created in the Generate the Okta API token step.
- okta_org_url. Enter your Okta URL. Note that the URL starts with https, and not http.
- stream_pos_path. Replace the
${path}variable with the actual path on the server where SumoJanus is installed. For example: '/home/sumojanus' - Save your changes. Your
sumojanus/conf/sumologic.propertiesfile should look similar to this example:
Step 5: Configure a Collector (DEPRECATED)
To avoid errors, use the latest bundled JRE version listed in the Collector Release Notes. Since the JRE folder can change with collector upgrades, we strongly recommend copying this JRE folder to a separate place and pointing the JAVAPATH to that folder. To check the current JRE folder the collector is using, go to the collector folder under config/wrapper.conf, and look for the variable wrapper.java.command.
Configure an Installed Collector on a Linux or Windows machine. By default the Collector will come with a Java Runtime Environment. To ensure that SumoJanus can locate Java, you may need to update the .bat or .bash file, as described below.
On Windows, update SumoJanus_Okta.bat
Navigate to the folder where you installed SumoJanus, and open SumoJanus_Okta.bat in a text editor. Line 3 of the script sets JAVAPATH to C:Program FilesSumo Logic Collectorjrebin as shown below:
set JAVAPATH='C:Program FilesSumo Logic Collectorjrebin'
If your collector JRE is in a different location, update Line 3 accordingly.
On Linux, update SumoJanus_Okta.bash
Navigate to the folder where you installed SumoJanus, and open SumoJanus_Okta.bash in a text editor. Update the script as follows:
- Add a line that sets
JAVA_HOMEto point to the location of your JRE, just before the last line of the script. For example, if your collector's JRE is in/opt/SumoCollector/jre/bin, insert this line:JAVA_HOME=/opt/SumoCollector/jre/bin The last line of the script is:
java -jar ${SUMOJANUS_JAR_FILE} ${runMode} OktaCollector-1.0.2.jar -e 1800
Prefix the line with$JAVA_HOME/, like this:$JAVA_HOME/java -jar ${SUMOJANUS_JAR_FILE} ${runMode} OktaCollector-1.0.2.jar -e 1800
Step 6: Configure a Source (DEPRECATED)
For guidance creating your Source Category naming convention, see Best Practices: Good Source Category, Bad Source Category.
To configure a Script Source, do the following:
Configure a Script Source. Collectors using version 19.245-4 and later do not allow Script Sources to run by default.
To allow Script Sources you need to set the Collector parameterenableScriptSourcein user.properties to true and restart the Collector.Linux
Windows
- Configure the Source fields:
- Name. OktaCollector.
- (Optional) Description.
- Source Category. okta
- Frequency. Every 5 Minutes
- Specify a timeout for your command. Activate the checkbox and select 60 Minutes
- Command. For Linux, use
/bin/bash.For windows, use Windows Script. (Specify the correct path on your system). - Script. Use the absolute path to sumojanus that you created in the Deploy the Packages step, such as
/home/ubuntu/sumojanus/bin/SumoJanus_Okta.bash.(Do not select 'Type the script to execute.') - Working Directory.
$path/sumojanus,where $path is the absolute path of SumoJanus that you created in the Deploy the Packages step.
Click Save.
Query samples
Details of Applications Deleted
_sourceCategory = 'okta' 'application.lifecycle.delete'
| json field=_raw 'eventType' as event_type
| where event_type = 'application.lifecycle.delete'
| json field=_raw 'outcome.result' as outcome_result
| json field=_raw 'displayMessage' as display_message
| json field=_raw 'published'as published_time
| json field=_raw 'actor.displayName' as okta_user_name
| json field=_raw 'actor.alternateId' as okta_user_id
| json field=_raw 'actor.type'
| json field=_raw 'severity' as severity
| json field=_raw 'target[0].displayName' as app_name
| json field=_raw 'target[0].type' as app_type
| json field=_raw 'client.ipAddress' as client_ip
| json field=_raw 'client.geographicalContext.city' as city
| json field=_raw 'client.geographicalContext.state' as state
| json field=_raw 'client.geographicalContext.country' as country
| json field=_raw 'client.geographicalContext.postalCode' as postal_code
| count by app_name, okta_user_id, outcome_result, display_message
Details of MFA Deactivate Event
_sourceCategory = 'okta' 'user.mfa.factor.deactivate'
| json field=_raw 'eventType' as event_type
| where event_type = 'user.mfa.factor.deactivate'
| json field=_raw 'outcome.result' as outcome_result
| json field=_raw 'published' as published_time
| json field=_raw 'actor.displayName' as actor
| json field=_raw 'actor.alternateId' as actor_id
| json field=_raw 'actor.type'
| json field=_raw 'severity' as severity
| json field=_raw 'client.userAgent.os' as OS
| json field=_raw 'client.userAgent.browser' as browser
| json field=_raw 'client.device' as device
| json field=_raw 'client.ipAddress' as client_ip
| json field=_raw 'client.geographicalContext.country' as country
| json field=_raw 'client.geographicalContext.state' as state
| json field=_raw 'client.geographicalContext.city' as city
| json field=_raw 'target[0].displayName' as okta_user_name
| json field=_raw 'target[0].alternateId' as okta_user_id
| count by okta_user_id, actor, outcome_result, country, state
Testing the Cisco RADIUS ASA VPN integrations involves two configuration tests: Single step and two-step flows. The following network diagrams represent these flows.
Topics
Flow diagrams
Network Diagram – Multi-step Flow
Network Diagram – Single-step Flow
Verify the Cisco ASA VPN Appliance is properly configured to work with Okta (two-step flow)
There are two parts to this test.
Part 1 – Test SSL-VPN with Cisco AnyConnect
Open Cisco AnyConnect and click Connect, as shown below.
Note
The username must be in the format you specified when you added the app in Okta in Part 2, above.
- Enter your Username, Password, and optionally, a Group, and click OK, as shown below.
- The username must be in the format you specified when you added the app in Okta in Part 2, above.
- If configured, you concatenate the Password with a one-time password (OTP) or a keyword; for example Password1,123456, Password1,push, or Password1,sms, as detailed below.
- 123456 – code from Okta Verify, Google Authenticator, or Yubikey OTP
- push – trigger push notice to enrolled phone
- sms – trigger sms to enrolled phone
- other – any other configuration
- If you receive the Login Failed screen, check you username and password and try again.
When the challenge screen appears, enter the corresponding number to the appropriate second factor and click Continue, as shown below. Follow the prompts to enter the second factor challenge.
Note
Users are challenged for a second factor to use based on the devices they have enrolled.
After successfully completing the challenge, you are connected and see the screen shown below.
If you enter an incorrect value or take to long to respond to the push notification, you see the screen shown below.
Test the clientless VPN with the AnyConnect web portal
Okta Anyconnect Login
- Navigate to the Cisco AnyConnect web portal URL, as shown below.
- Enter the same username, password, and group (optional), as in part 1, above.
- Enter the challenge factors when prompted.
After successfully completing the challenge, you are connected and see the screen shown below.
If you enter an incorrect value or take to long to respond to the push notification, you see the screen shown below.
Verify the Cisco ASA VPN Appliance is properly configured to work with Okta (single-step flow)
There are two parts to this test.
Okta Anyconnect Login
Part 1 – Test SSL-VPN with Cisco AnyConnect
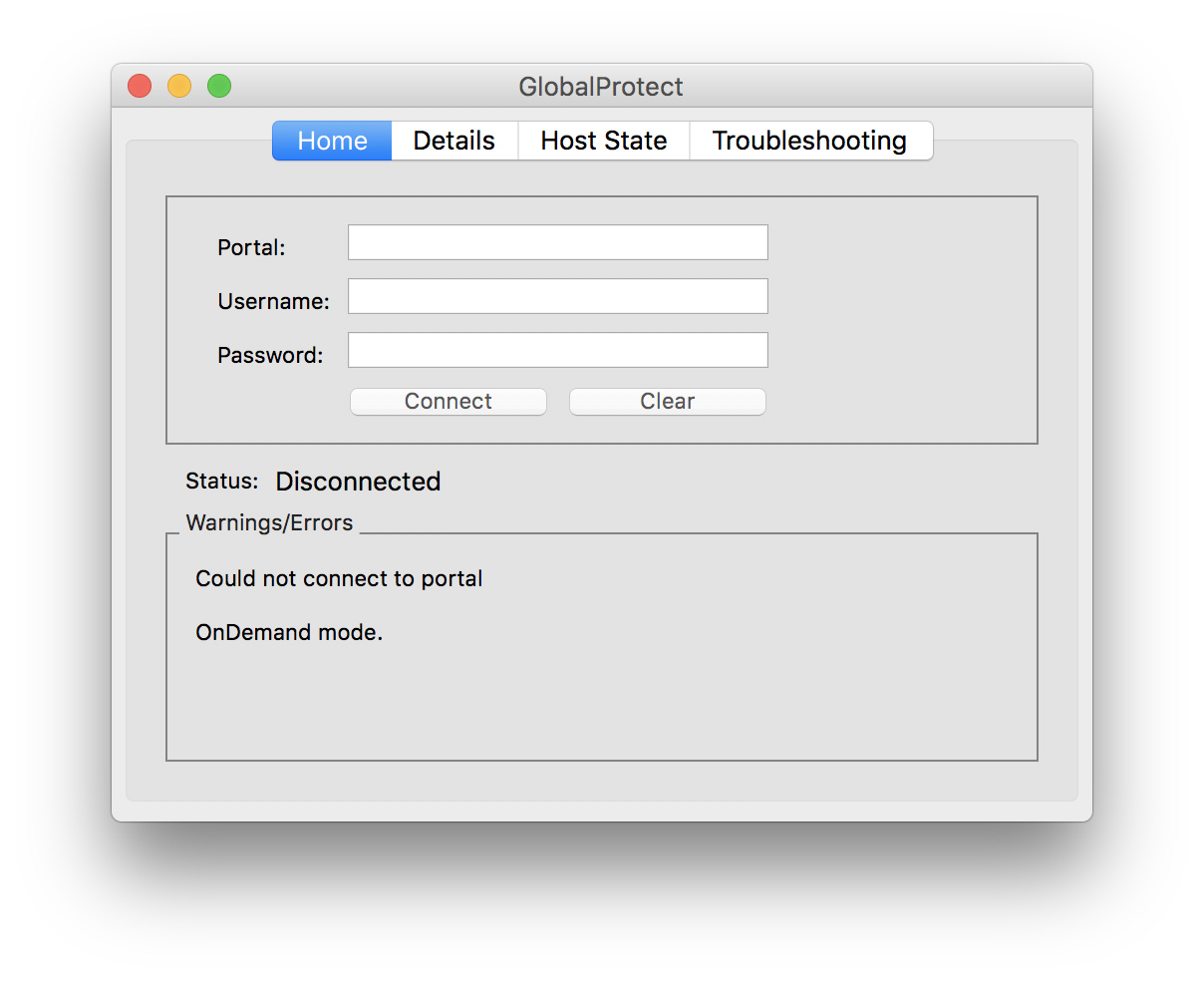
Open Cisco AnyConnect and click Connect, as shown below.
Note
The username must be in the format you specified when you added the app in Okta in Part 2, above.
- Enter your Username, Password,Second Password, and optionally, a Group, and click OK, as shown below.
- The username must be in the format you specified when you added the app in Okta in Part 2, above.
- Enter the second password, as follows.
- 123456 – Code from Okta Verify, Google Authenticator, or Yubikey OTP
- push – trigger push notice to enrolled phone
- sms – trigger sms to enrolled phone
- other – any other configuration
- If you receive the Login Failed screen, check you username and password and try again.
After successfully completing the challenge, you are connected and see the screen shown below.
If you enter an incorrect value or take to long to respond to the push notification, you see the screen shown below.
Part 2 –Test the clientless VPN with the AnyConnect web portal
- Navigate to the Cisco AnyConnect web portal URL, as shown below.
- Enter your Username, Password,Second Password, and optionally, a Group, and click OK, as shown below.
- The username must be in the format you specified when you added the app in Okta in Part 2, above.
- Enter the second password, as follows.
- 123456 – Code from Okta Verify, Google Authenticator, or Yubikey OTP
- push – trigger push notice to enrolled phone
- sms – trigger sms to enrolled phone
- other – any other configuration
- If you receive the Login Failed screen, check you username and password and try again.
After successfully completing the challenge, you are connected and see the screen shown below.
If you enter an incorrect value or take to long to respond to the push notification, you see the screen shown below.
